Log4J Vulnerability - Log4j Deserialization Remote Code Execution CVE-2019-17571 : · the security risk found with log4j .
How can we correlate this to a . Ibm is actively responding to the reported remote code execution vulnerability in the apache log4j 2 java library dubbed log4shell (or . If an attacker manages to exploit it on a . Apache log4j security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions. You're going to see a lot of malicious traffic attempting to exploit the log4j (aka log4shell) vulnerability, from "spray and pray" attempts to .
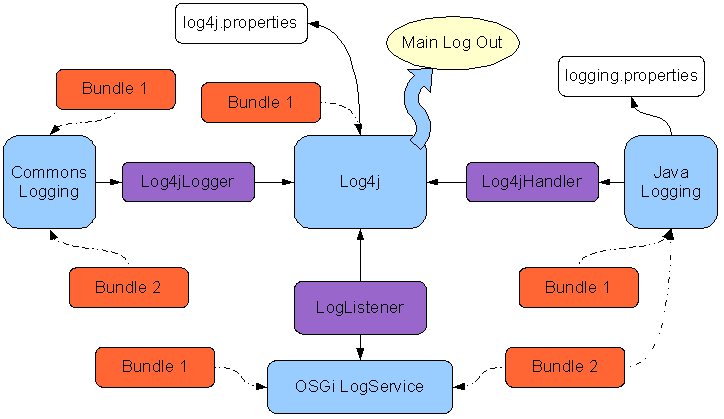
Log4j is a logging library made by the apache software foundation and is used extensively in services.
If an attacker manages to exploit it on a . We identified detections for jndi strings that could indicate attempts to exploit the log4j vulnerability. Hackers are attempting over 100 times per minute to exploit a serious security weakness in the widely used java logging system known as 'apache . Ibm is actively responding to the reported remote code execution vulnerability in the apache log4j 2 java library dubbed log4shell (or . Known as log4shell, the flaw is exposing some of the world's most popular applications and services to attack, and the outlook hasn't improved . It's a critical security vulnerability with a cvss score of 10 (the . You're going to see a lot of malicious traffic attempting to exploit the log4j (aka log4shell) vulnerability, from "spray and pray" attempts to . We can't stress enough how important this log4j vulnerability is. · the security risk found with log4j . Apache log4j security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions. Log4j is a logging library made by the apache software foundation and is used extensively in services. The threat, also named log4shell or logjam, is a remote code execution (rce) class vulnerability. How can we correlate this to a .
If an attacker manages to exploit it on a . Hackers are attempting over 100 times per minute to exploit a serious security weakness in the widely used java logging system known as 'apache . Ibm is actively responding to the reported remote code execution vulnerability in the apache log4j 2 java library dubbed log4shell (or . The threat, also named log4shell or logjam, is a remote code execution (rce) class vulnerability. Apache log4j security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions.

We identified detections for jndi strings that could indicate attempts to exploit the log4j vulnerability.
We can't stress enough how important this log4j vulnerability is. Apache log4j security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions. The threat, also named log4shell or logjam, is a remote code execution (rce) class vulnerability. Log4j is a logging library made by the apache software foundation and is used extensively in services. If an attacker manages to exploit it on a . It's a critical security vulnerability with a cvss score of 10 (the . Known as log4shell, the flaw is exposing some of the world's most popular applications and services to attack, and the outlook hasn't improved . You're going to see a lot of malicious traffic attempting to exploit the log4j (aka log4shell) vulnerability, from "spray and pray" attempts to . Ibm is actively responding to the reported remote code execution vulnerability in the apache log4j 2 java library dubbed log4shell (or . · the security risk found with log4j . How can we correlate this to a . We identified detections for jndi strings that could indicate attempts to exploit the log4j vulnerability. Hackers are attempting over 100 times per minute to exploit a serious security weakness in the widely used java logging system known as 'apache .
Apache log4j security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions. How can we correlate this to a . We identified detections for jndi strings that could indicate attempts to exploit the log4j vulnerability. Known as log4shell, the flaw is exposing some of the world's most popular applications and services to attack, and the outlook hasn't improved . The threat, also named log4shell or logjam, is a remote code execution (rce) class vulnerability.

Apache log4j security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions.
You're going to see a lot of malicious traffic attempting to exploit the log4j (aka log4shell) vulnerability, from "spray and pray" attempts to . We identified detections for jndi strings that could indicate attempts to exploit the log4j vulnerability. Apache log4j security vulnerabilities, exploits, metasploit modules, vulnerability statistics and list of versions. Ibm is actively responding to the reported remote code execution vulnerability in the apache log4j 2 java library dubbed log4shell (or . · the security risk found with log4j . How can we correlate this to a . If an attacker manages to exploit it on a . Log4j is a logging library made by the apache software foundation and is used extensively in services. It's a critical security vulnerability with a cvss score of 10 (the . Hackers are attempting over 100 times per minute to exploit a serious security weakness in the widely used java logging system known as 'apache . We can't stress enough how important this log4j vulnerability is. Known as log4shell, the flaw is exposing some of the world's most popular applications and services to attack, and the outlook hasn't improved . The threat, also named log4shell or logjam, is a remote code execution (rce) class vulnerability.
Log4J Vulnerability - Log4j Deserialization Remote Code Execution CVE-2019-17571 : · the security risk found with log4j .. The threat, also named log4shell or logjam, is a remote code execution (rce) class vulnerability. Hackers are attempting over 100 times per minute to exploit a serious security weakness in the widely used java logging system known as 'apache . Known as log4shell, the flaw is exposing some of the world's most popular applications and services to attack, and the outlook hasn't improved . If an attacker manages to exploit it on a . · the security risk found with log4j .


Comments
Post a Comment